Cybersecurity in medical devices - Part 3 AAMI TIR57:2016
By Mitch on Tuesday, 16 May 2017, 21:53 - Standards - Permalink
After a long pause, we continue this series about cybersecurity in medical devices with a discussion on AAMI TIR57:2016 Principles for medical device security — Risk management.
This TIR is the one and only document available in the corpus on medical device-related standards and guidances, dealing with the application of cybersecurity principles and their impact on ISO 14971 risk management process. Yet, FDA guidances exist, but they’re not as direct as this TIR to show the impact of cybersecurity management process on risk management process.
Structure of AAMI TIR57:2016
The structure of sections 3 to 9 of this document is copied from ISO 14971 standard. It shows how the security risk management process can be modeled in a manner similar to the safety risk management process.
If you’re at ease with ISO 14971, you’ll be at ease with AAMI TIR57. Your effort of understanding will be focused on security risk management concepts, not the process (risk identification, evaluation, mitigation and so on…) that you already know.
We can bless the working group in charge of this TIR for this effort of presentation. The diagram below, extracted from the TIR, shows the analogy between both processes.
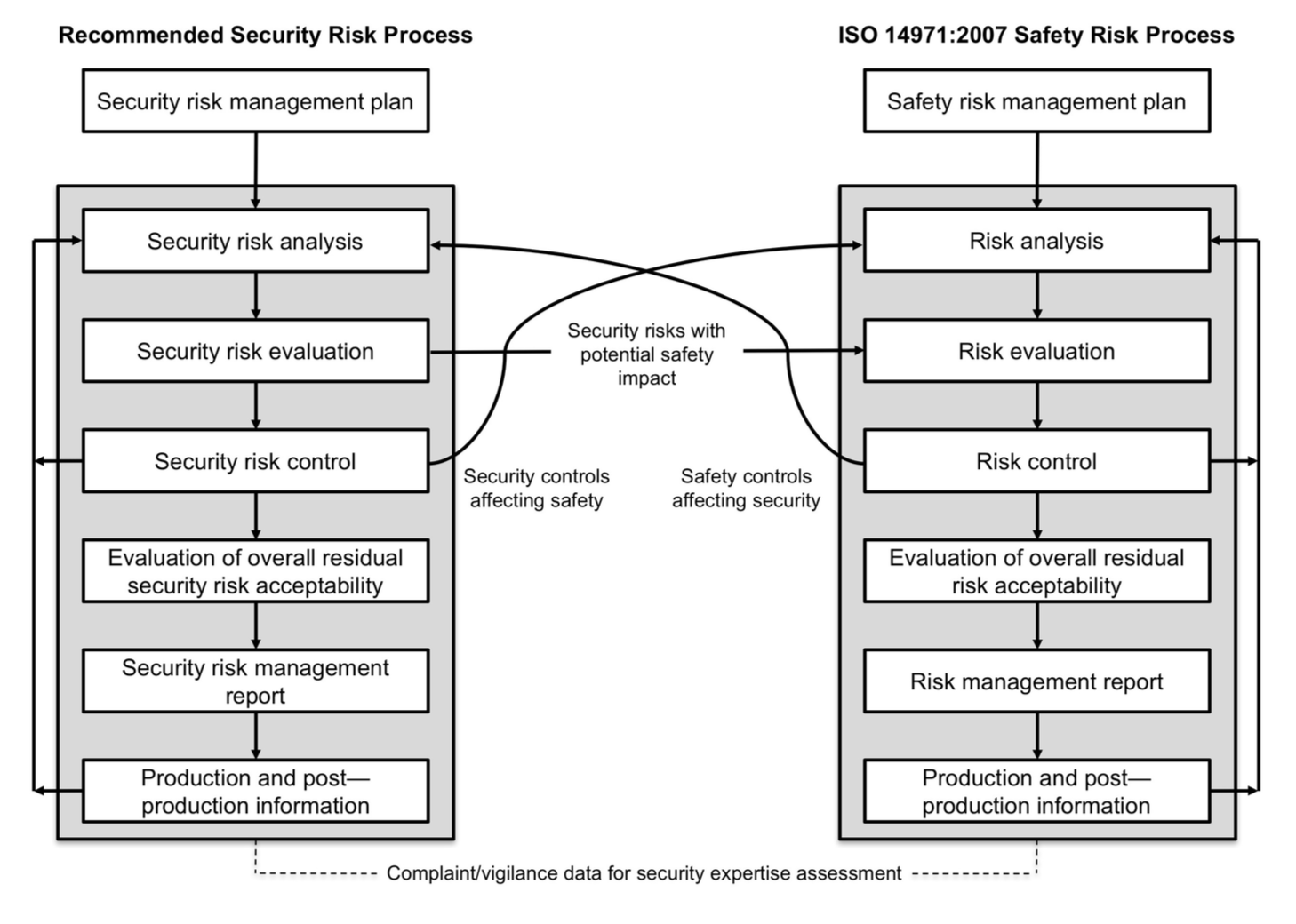
You've probably already seen this diagram elsewhere. And I bet that many articles or newsletters dealing cybersecurity in medical devices are going to reproduce it as well!
Separation of processes
The TIR recommends to separate the security and safety risk management processes. This looks as a good recommendation, as people involved in both processes are not all the same. Data security and clinical safety concepts are not managed by the same persons with the same qualifications.
Cons
This separation is going to remain very theoretical for most of small businesses. Practically, big companies can afford maintaining two processes and the needed qualified persons, but small businesses don’t.
Small businesses will require the help of security experts to manage security risks. But they will be most probably hired as consultants. People who currently manage ISO 14971 process will manage both processes, without clear separation on a day to day basis.
Pros
The separation of processes is a good way to monitor efficiently security risk management. Keeping a security risk management file separated form the safety risk management file allows to document the outputs of the process without mixing concepts of security risk management (threats, vulnerabilities, assets, adverse impacts), with concepts of safety risk management (hazardous phenomenon, hazardous situation, hazard, harm).
Annexes of AMMI TIR:57:2016
The annexes found after section 9 are another wealth of information. They contain practical methods to implement a security risk management process. There is even a list of questions that can be used to identify medical device security characteristics, like the annex C of ISO 14971 for safety risks!
The TIR ends with an example based on a fictional medical device: the kidneato system, with everything that a manufacturer shouldn’t do: an implanted part, a part connected to the public network, and a server storing medical data. Delicatessen for hackers!
Multiplication of risk management files
With the ongoing implementation of ISO 13485:2016 by medical device manufacturers, another consequence of security risk management is the multiplication of risk management files:
- QMS Process risk management,
- Safety risk management,
- Security risk management, and
- Risk / opportunities management, for the fans of ISO 9001:2015.
We can even try to draw a table of interactions between these processes (I skip ISO 9001:2015, but don’t conclude I’m not a fan :-))
| Affects | Safety | QMS Process | Security | |
| Risks | ||||
| Safety | X | Safety risk mitigations implemented in QMS processes | Safety risks with potential impact on security. Safety controls affecting security | |
| QMS Process | Hazardous situations in QMS processes with impact on safety. QMS process controls affecting safety | X | QMS process risk controls affecting security. Threats, vulnerabilities, assets found in processes to assess in security risk management | |
| Security | Security risks with impact on safety, Security controls affecting safety | Security risks with impacts on QMS processes (and possibly safety). Security controls affecting QMS processes | X | |
Conclusion
AAMI TIR75:2016 is an excellent source of information for newbies in security risk management. A must-read for people not qualified in security risk management, who need to manage the process, and anticipate its impact on other processes.
In the next article, we’ll see the consequence of cybersecurity management on software development and maintenance processes.

Comments
Hi Mitch, thanks for the overview of AAMI TIR57:2016 Principles for medical device security — Risk management. A really easy to follow summary. Is this harmonised (EU MDR [pov), or do you think it will likely be harmonsied in the future?
Also i'd be interested to know whether you think the Security of Network & Informations Systems Directive 2016/1148 aka the Cybersecurity directive (to be implemented into member states by ~end 2018) will have a direct effect on medical device manufacturers?
Hi Ben,
No, it won't be harmonized, it is a US document. But it can be used as state-of-the-art for implementation of cybersecurity for other regulations.
The cybersecurity directive addresses security of networks of operators of vital importance: power plants, telco infrastructure, and possibly hospitals (I'm not a specialist). It's not directly applicable to MD manufacturers.